Data Security & Compliance
SOC 2 Type 2 Certification
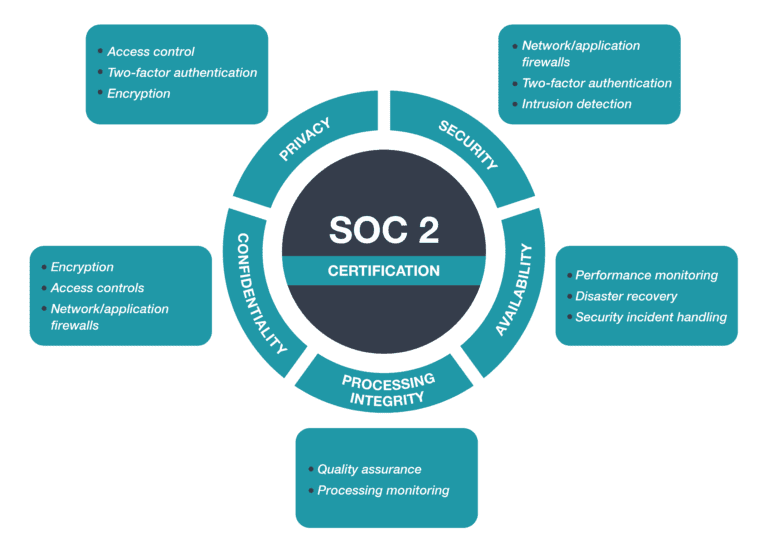
fullthrottle.ai® delivers a SOC 2 compliant platform, following the SOC 2 principles of Privacy, Security, Availability, Processing Integrity, and Confidentiality.
SOC 2 (Service and Organization Controls 2) is a set of security and privacy standards that organizations can follow to demonstrate their commitment to protecting sensitive customer data. The SOC 2 standards are published by the American Institute of Certified Public Accountants (AICPA).
Request the SOC 2 Report
What you get with fullthrottle.ai®
Culture of Security

Proactive Security Posture & Monitoring of National/Global Tech Security Events
24/7 Automated Infrastructure Security Perimeter Monitoring + Alerting. Daily Monitoring of Industry Notifications, Including CISA.
Daily Operational Reviews
- Traffic Monitoring via Active WAF ACLs etc
- Perimeter Monitoring – AWS GuardDuty, CloudWatch etc
- Data Security Review Committee
- Risk Management Review Meetings
- Bi-Monthly Leadership SecOps Review Meetings
Monthly Server Configuration Audits
- Defined Incident Response Teams and Procedures
- External Independent Penetration Tests
Attestation and Team Awareness
24/7 Automated Infrastructure Security Perimeter Monitoring + Alerting.
SOC 2 Type 2 Attestation and SOC 2 Policies
- NIST Based Controls
Security and Standards Training
- Phishing and Other Credential Breach Awareness Training
- OWASP Code Development Standards Applied
- Automated Application Credential Rotation and File Handling Standards


Access Control
Daily Monitoring of Industry Notifications, Including CISA.
Daily Operational Reviews
- Principle of Least Privilege
- Infrastructure Access Behind 2FA
- Password Policies and Rotation
- Role-Based User Access
- User System Access Audits
- User System Permission Audits
What you get with fullthrottle.ai®
Key Security Principles Applied

Infrastructure Security
- Logical Network Separation
- Restricted Ports
- Appropriate IP restrictions
- Lightweight Server Configurations
- Approved File Extension Control on Application Servers

Data Security
- Data Encryption at Rest and In Flight
- Data Classification and Handling Policy and Procedures
- Monthly Data Classification Audit
- Privacy Data Classification and Handling

Availability
- Daily (continual) Process Capacity and Availability Monitoring
- Backup Schedules
- Maintain Recovery Infrastructure
- Quarterly Disaster Recovery Testing

Process Monitoring
Infrastructure, user event logging, and user access audits. Weekly as well as monthly infrastructure monitoring.
Data Retention & Remediation
Client Data Retention policies are observed and practiced first when provided in onboarding, otherwise:
- Active client data is retained for 7 years, then archived or deleted automatically.
- Inactive client data is deleted or archived after 24 months of inactivity, records are kept for audits and compliance, unless otherwise directed.
- Automated processes manage data deletion and archiving monthly.
Major purchases aren’t made alone — families and households research together across devices. Immersive Household® delivers ads across all household devices, ensuring your message stays visible and relevant.

Building trust & peace of mind for our partners
SOC 2 demonstrates fullthrottle.ai’s commitment to security and privacy. By demonstrating SOC 2 compliance, we can reassure our customers that their sensitive information is being handled responsibly and securely. We can provide peace of mind to organizations, knowing that we have taken appropriate measures to secure and protect sensitive information. This can help organizations sleep better at night, knowing that they have taken the necessary steps to protect their customers’ information.

Compliance requirements & cost savings
In certain industries, SOC 2 compliance may be a requirement for doing business. We can demonstrate SOC 2 compliance for all industries. Additionally, implementing the controls required for SOC 2 compliance can help streamline security and privacy practices. By taking a proactive approach to security and privacy, we can avoid the costs associated with security incidents and data breaches that are now minimized with our proactive frameworks.
Improved security posture & internal processes
The SOC 2 standards provide a framework for fullthrottle.ai® to improve their security posture by identifying and addressing potential risks to sensitive information. By following the SOC 2 standards, we can reduce the likelihood of security incidents and data breaches. SOC 2 also gives us a framework to continually improve our internal processes and procedures, which helps us operate more efficiently and effectively.
Frequently Asked Questions
Your Next Buyer Is Already Browsing
Reach them instantly with omnichannel media activations, track what works, and grow with confidence.