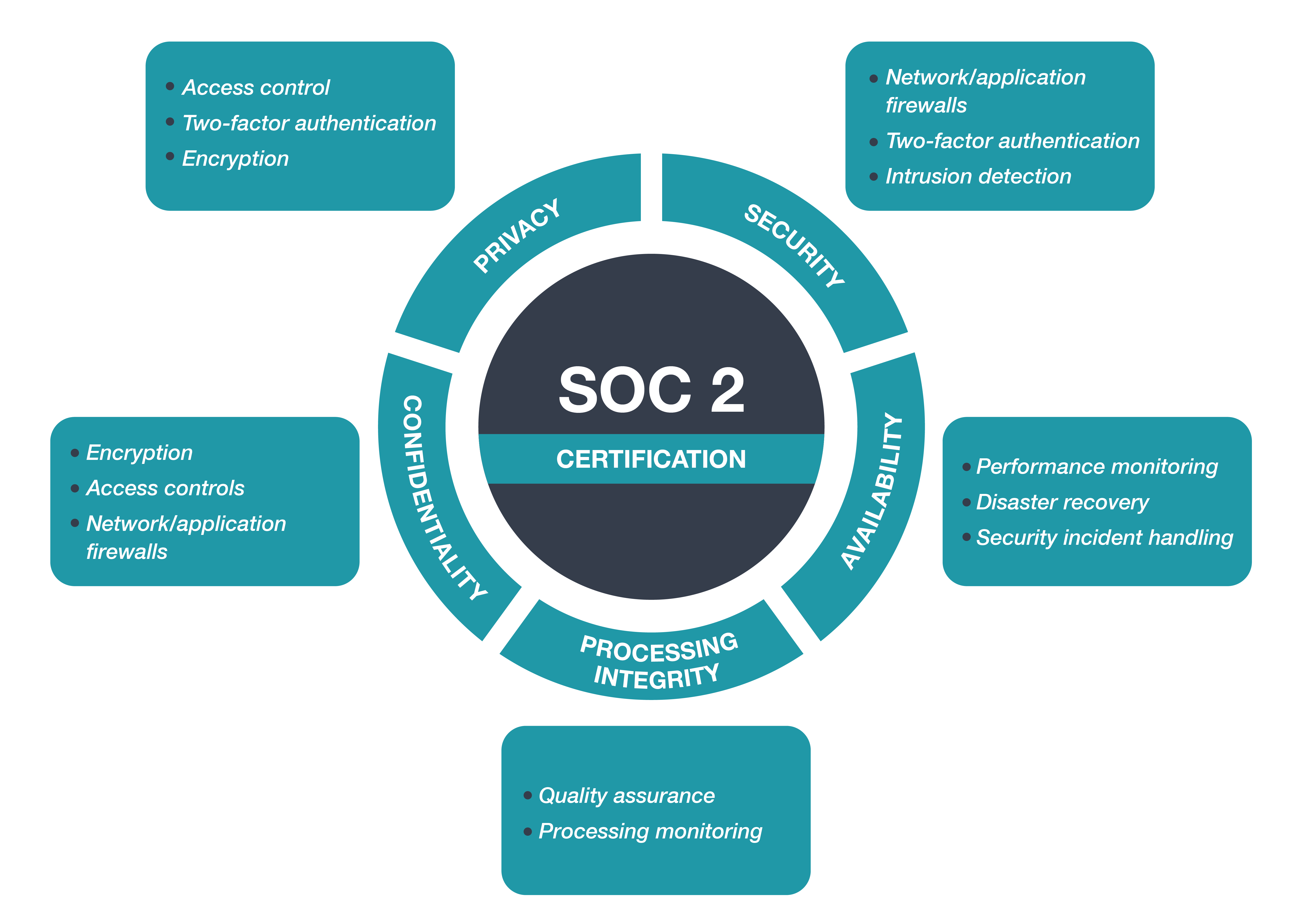
SOC 2 Type 2 Certification
fullthrottle.aiTM delivers a SOC 2 compliant platform, following the SOC 2 principles of Privacy, Security, Availability, Processing Integrity, and Confidentiality.
SOC 2 (Service and Organization Controls 2) is a set of security and privacy standards that organizations can follow to demonstrate their commitment to protecting sensitive customer data. The SOC 2 standards are published by the American Institute of Certified Public Accountants (AICPA).
Culture of Security

Proactive Security Posture
- 24/7 Automated Infrastructure Security Perimeter Monitoring + Alerting
- Daily Operational Reviews
- Traffic Monitoring via Active WAF ACLs etc
- Perimeter Monitoring – AWS GuardDuty, CloudWatch etc
- Monthly Server Configuration Audits
- Defined Incident Response Teams and Procedures
- External Independent Penetration Tests

Proactive Monitoring of National/Global Tech Security Events
- Daily Monitoring of Industry Notifications Including CISA
- Data Security Review Committee
- Risk Management Review Meetings
- Bi-Monthly Leadership SecOps Review Meetings

Attestation and Team Awareness
- SOC 2 Type 2 Attestation and SOC 2 Policies
- NIST Based Controls
- Security and Standards Training
- Phishing and Other Credential Breach Awareness Training
- OWASP Code Development Standards Applied
- Automated Application Credential Rotation and File Handling Standards

Access Control
- Principle of Least Privilege
- Infrastructure Access Behind 2FA
- Password Policies and Rotation
- Role Bases User Access
- User System Access Audits
- User System Permission Audits
Key Security Principles Applied

Infrastructure Security
- Logical Network Separation
- Restricted Ports
- Appropriate IP restrictions
- Lightweight Server Configurations
- Approved File Extension Control on Application Servers

Data Security
- Data Encryption at Rest and In Flight
- Data Classification and Handling Policy and Procedures
- Monthly Data Classification Audit
- Privacy Data Classification and Handling

Process Monitoring
- Infrastructure and User Event Logging
- Weekly and Monthly Infrastructure and User Access Audits

Availability
- Daily (continual) Process Capacity and Availability Monitoring
- Backup Schedules
- Maintain Recovery Infrastructure
- Quarterly Disaster Recovery Testing
Building trust & peace of mind for our partners
SOC 2 demonstrates fullthrottle.ai's commitment to security and privacy. By demonstrating SOC 2 compliance, we can reassure our customers that their sensitive information is being handled responsibly and securely. We can provide peace of mind to organizations, knowing that we have taken appropriate measures to secure and protect sensitive information. This can help organizations sleep better at night, knowing that they have taken the necessary steps to protect their customers' information.

Compliance requirements & cost savings
In certain industries, SOC 2 compliance may be a requirement for doing business. We can demonstrate SOC 2 compliance for all industries. Additionally, implementing the controls required for SOC 2 compliance can help streamline security and privacy practices. By taking a proactive approach to security and privacy, we can avoid the costs associated with security incidents and data breaches that are now minimized with our proactive frameworks.
Improved security posture & internal processes
The SOC 2 standards provide a framework for fullthrottle.aiTM to improve their security posture by identifying and addressing potential risks to sensitive information. By following the SOC 2 standards, we can reduce the likelihood of security incidents and data breaches. SOC 2 also gives us a framework to continually improve our internal processes and procedures, which helps us operate more efficiently and effectively.

Frequently Asked Questions
What is SOC 2?
SOC 2 (Service and Organization Controls 2) is a set of security and privacy standards that organizations can follow to demonstrate their commitment to protecting sensitive customer data. The SOC 2 standards are published by the American Institute of Certified Public Accountants (AICPA).
Why is SOC 2 important?
SOC 2 is important because it provides assurance to customers and other stakeholders that an organization has taken appropriate measures to secure and protect sensitive information. By demonstrating SOC 2 compliance, organizations can build trust with customers and increase their competitiveness in the marketplace.
What are the SOC 2 requirements?
The SOC 2 requirements cover five trust service principles: security, availability, processing integrity, confidentiality, and privacy. Organizations must have policies and procedures in place to demonstrate their adherence to these principles and undergo regular audits to prove their compliance.
What does it take to achieve SOC 2 compliance?
Development of policies and procedures, the implementation of controls, and the documentation of evidence.
How often is SOC 2 compliance required?
SOC 2 compliance is typically required annually. The SOC 2 standards are constantly evolving to keep pace with changes in technology and the threat landscape, which means that organizations must continually assess and update their controls to maintain compliance. SOC 2 compliance requires a continued commitment to security and privacy best practices.
What is the difference between SOC 2 and SOC 3?
SOC 2 is a more in-depth and comprehensive set of security and privacy standards, while SOC 3 is a summary of SOC 2 that provides a broader view of an organization's security and privacy practices. SOC 3 is designed for organizations that want to provide general information about their security and privacy practices to a wider audience, while SOC 2 is designed for organizations that want to provide detailed information to customers and other stakeholders.
Who performs the SOC 2 audit?
An independent third-party auditor performs an SOC 2 compliance audit. The auditor will review the policies and procedures, assess the implementation of the controls, and test the effectiveness of the controls.
What policies and procedures are required for SOC 2 compliance?
An organization must have policies and procedures that are designed to meet the five trust service principles: security, availability, processing integrity, confidentiality, and privacy.
What risk assessments are needed?
A risk assessment to identify potential security and privacy risks and determine the controls that are needed to mitigate those risks.
What controls are required?
Based on the risk assessment, the organization must implement controls to address identified risks. These controls could include network security measures, access controls, data encryption, and data backup and recovery procedures.
What evidence must be documented?
The organization must document evidence that the controls are in place and functioning effectively. This documentation should include descriptions of the policies and procedures, a list of the controls that have been implemented, and the results of security testing and monitoring activities.